Zero-Trust at the Edge: Securing Distributed Apps Without Slowing Them Down
How modern teams protect users, data, and devices across thousands of locations—without adding latency.
Why Zero-Trust Moves to the Edge
Zero-Trust began as a response to a simple reality: the network perimeter disappeared.
By 2025, that reality has expanded again. Your “perimeter” now includes:
- Edge POPs and regional nodes
- Retail stores, ATMs, kiosks, factories
- Mobile devices, browsers, IoT gateways
- Third-party APIs and SaaS plugins
The mistake many teams make is implementing Zero-Trust only in the cloud—then forcing every request to traverse it. That creates security and performance problems.
The shift:
👉 Enforce Zero-Trust as close to the request as possible—at the edge.
When done right, Zero-Trust at the edge reduces latency, contains blast radius, and improves resilience.
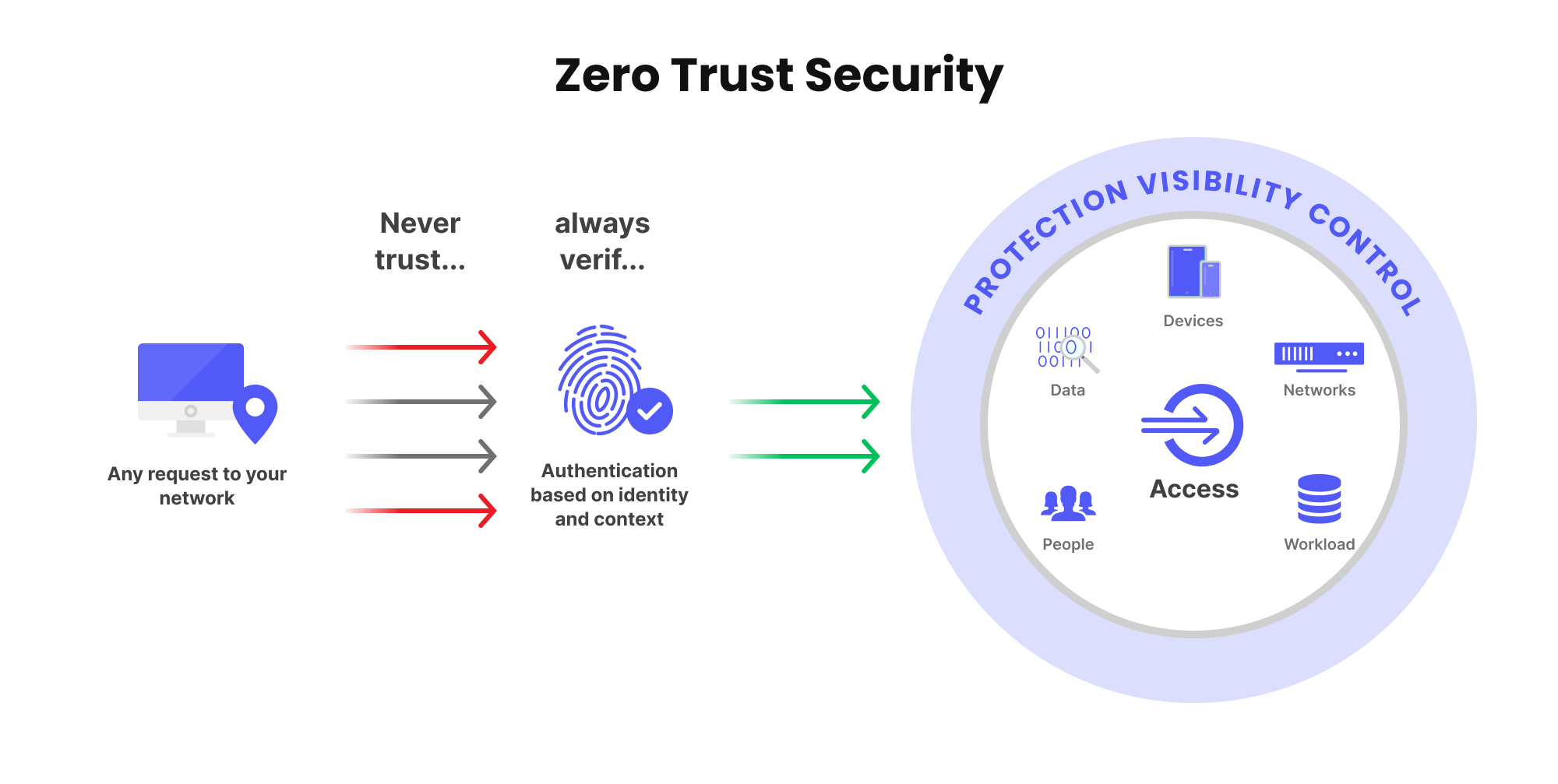
1. Zero-Trust, Re-defined for the Edge Era
Classic Zero-Trust principles still apply:
- Never trust, always verify
- Least privilege access
- Continuous evaluation
- Explicit identity and policy
But edge environments add new constraints:
| Cloud Zero-Trust | Edge Zero-Trust |
|---|---|
| Centralized | Highly distributed |
| Stable connectivity | Intermittent/offline |
| Few entry points | Thousands of entry points |
| Human users | Humans + devices + services |
Edge Zero-Trust must be:
✔ Stateless
✔ Fast (<20ms decisions)
✔ Policy-driven
✔ Resilient to disconnection
2. The Hidden Risk: Centralized Security Bottlenecks
Many organizations still do this:
- User → Edge
- Edge → Cloud IAM
- IAM → Policy engine
- Policy → Backend
- Response → Edge → User
That’s 4–6 hops per request.
What goes wrong:
- Latency spikes during traffic surges
- Auth systems become single points of failure
- Edge nodes turn into dumb pipes
- Attackers gain time to probe
Zero-Trust fails when it slows the system it’s protecting.
3. The Edge-Native Zero-Trust Model
The winning pattern looks like this:
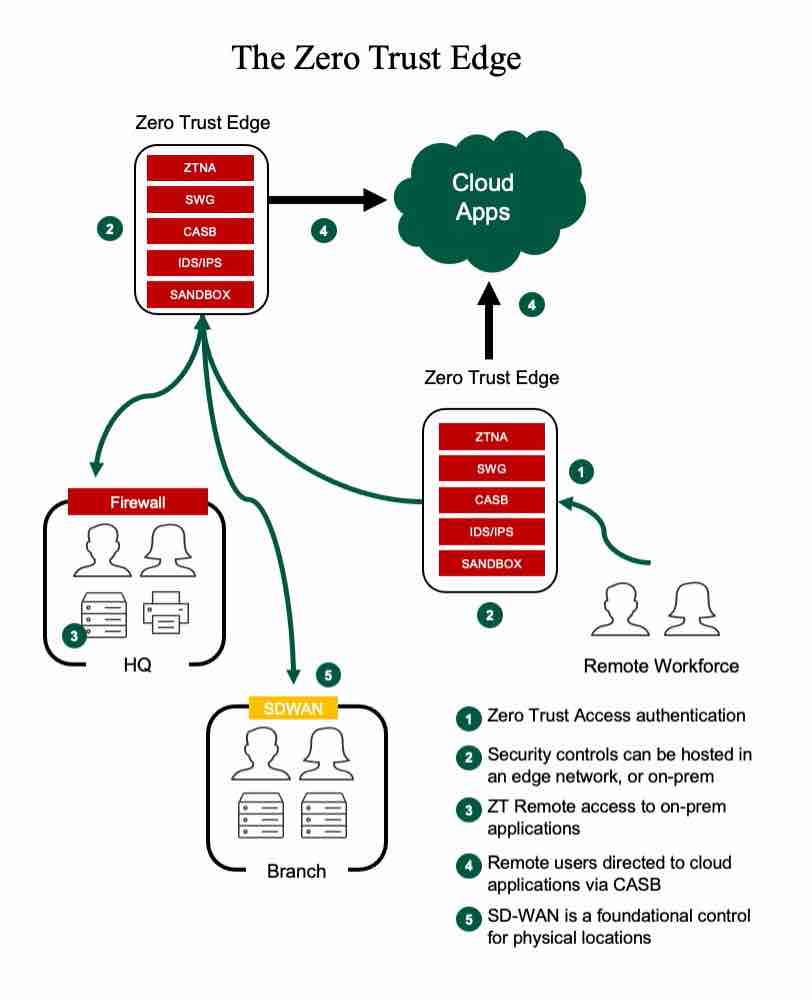

Decision hierarchy
- Edge: Identity validation + coarse policy
- Regional edge: Contextual policy + risk scoring
- Cloud: Deep inspection + analytics
80–90% of decisions never leave the edge.
4. Core Building Blocks of Zero-Trust at the Edge
A. Identity Everywhere (Not Just Users)
At the edge, identity applies to:
- Users
- Devices
- Services
- Locations
Best practices
- Short-lived JWTs or mTLS certs
- Device identity bound to hardware or TPM
- No IP-based trust—ever
Real-world insight
Retailers running store-level edge nodes often rotate device certificates every 24 hours, reducing credential reuse attacks dramatically.
B. Policy-as-Code at the Edge
Policies must be:
- Deterministic
- Versioned
- Locally enforceable
Examples
- “POS terminals can call pricing APIs only from store networks”
- “ATMs can approve withdrawals ≤ X without cloud round-trip”
- “IoT sensors can publish only whitelisted events”
Use engines like OPA-style policy logic compiled for edge runtimes.
Key rule:
If the policy can’t run offline, it doesn’t belong at the edge.
C. Continuous Trust Evaluation (Without Latency)
Instead of re-authenticating constantly:
- Validate token once at the edge
- Evaluate context signals locally:
- Device posture
- Geo consistency
- Request velocity
- Behavioral anomalies
Only high-risk requests escalate to deeper inspection.
This preserves security and speed.
5. Securing Edge-to-Cloud and Edge-to-Edge Traffic
mTLS Is Mandatory
- Every service has an identity
- Every connection is encrypted
- No shared secrets
Service segmentation
- Edge services can talk only to specific upstreams
- No lateral movement between edge nodes
Interesting fact
In large ATM networks, segmentation reduced malware propagation time from minutes to never—attacks simply couldn’t jump zones.
6. Zero-Trust for Edge Devices and IoT
Edge Zero-Trust must assume:
- Devices will be stolen
- Networks will be hostile
- Connectivity will drop
Best practices
✔ Secure boot + signed firmware
✔ Immutable edge OS
✔ Read-only root filesystems
✔ Local policy cache
✔ Automatic quarantine on drift
Offline-first security is not optional—it’s foundational.
7. Observability: Trust What You Can See
Security without visibility is theater.
Edge Zero-Trust requires:
- Local decision logs
- Signed policy versions
- Request traces with identity context
- Tamper-proof audit trails
Logs sync to cloud when available, not when required.
8. Performance Impact: Myth vs Reality
Myth: Zero-Trust slows things down
Reality: Edge Zero-Trust often speeds things up
Why?
- No centralized auth calls
- No long policy chains
- Fewer backend hops
- Early rejection of bad traffic
Teams report 20–40% latency improvements after moving auth and policy to the edge.
9. A Real Example: Zero-Trust in Retail Banking
A regional bank faced:
- ATM fraud attempts
- High auth latency during peak hours
- Regulatory pressure for local processing
What they changed
- Edge-based identity validation
- Local withdrawal policy enforcement
- Regional fraud scoring
- Cloud escalation only on anomalies
Results
- Decision latency: ~180ms → <60ms
- Fraud attempts blocked earlier
- Core IAM load reduced 65%
- No outages during peak usage
10. 30-60-90 Day Implementation Plan
Days 0–30
- Inventory identities (users, devices, services)
- Identify auth bottlenecks
- Select edge policy engine
Days 31–60
- Move token validation to edge
- Deploy policy-as-code
- Implement mTLS everywhere
Days 61–90
- Add behavioral risk scoring
- Enable offline enforcement
- Roll out observability dashboards
- Run chaos tests (disconnect edge from cloud)
11. Common Mistakes to Avoid
❌ Treating edge as untrusted forever
✔ Edge should be verified, not blind
❌ Hard-coding policies
✔ Policies must be dynamic and versioned
❌ Ignoring device identity
✔ Devices are first-class actors
❌ Centralizing incident response
✔ Edge must contain damage locally
Final Thought
Zero-Trust is no longer a network strategy—it’s a distributed systems discipline.
When enforced at the edge, Zero-Trust:
- Improves security posture
- Reduces blast radius
- Cuts latency
- Increases uptime
- Simplifies compliance
The safest systems in 2026 won’t be the most locked down.
They’ll be the ones that make trust decisions fastest—closest to where reality happens.





